Data breaches in healthcare become more of an issue recently. The industry sees an alarming growth in the number.
Let’s dive into the numbers. Back in 2017, 5.5 million patient records were disclosed from 477 cases of reported data breaches, according to Protenus Breach Barometer.
A year later, the number of breached patient record almost tripled and consisted of 15 million files from 507 registered cases.
The Atrium Health breach was the biggest reported incident with 2.65 million disclosed records. It was registered in November, the cause was a hack on AccuDoc Solutions, their billing vendor. Patient data remained open for about a week.
In 2019, the numbers began to frow exponentially – to 41.4 million patient records breached, with an impressive 49 percent increase in hacking.
The security researchers noted that though the ransomware attacks rate is equal to the one seen at the end of 2019.
Healthcare solutions developers should not be relaxed.
They still have plenty of room for improvement when it comes to securing remote connections, taking care of storing and transferring the documents, and educating staff to prevent the frequency of successful phishing attacks.
The speed and frequency of breach reporting also remain imperfect.
This blog post is the continuation of our article series about cybersecurity in healthcare.
Here we will tell you about the biggest incidents of patient data being exposed, describe the main reasons for it, and, by diving deep into the Verizon Data Breach Investigation Report, will figure the main patterns of what’s going on in the sector.
The Biggest US Healthcare Data Breaches of 2020 to Date
We’ve decided to dive into the biggest data breaches in the healthcare industry.
The resource HealthItSecurity stores data about them, and according to this list, the biggest data breaches in US healthcare happened in Oregon, Florida, and Indiana.
Health Share of Oregon: 654,000 Patients Suffered
The biggest data leak to date happened due to the theft of a laptop owned by the transportation vendor of Health Share, the largest Medicaid coordinated care organization in Oregon.
This fact shows that physical security controls and vendor management need to be treated with the same seriousness other cybersecurity activities are done. The report about the incident did not clarify whether the laptop was encrypted, but our lucky guess would be inclined to the negative side of the spectrum.
The stolen computer had information about patient names, contact details, dates of birth, Medicaid ID numbers, and Social Security numbers. Health histories were not stored on the laptop.
As a result of the incident, Health Share updated its annual audit processes with its contractors and improved workforce training.
Florida Orthopaedic Institute: 640,000 Patients’ Data Stolen
A ransomware attack on the Florida Orthopaedic Institute (FOI) potentially breached the data of about 640,000 patients and was first reported on July,1st
The attack was first discovered on April 9, with the malware encrypting data stored on FOI servers.
The staff of the Institute was able to quickly secure the system, but the investigation found that patient data was potentially accessed during the attack.
The information stored in the data may have included names, dates of birth, social security numbers, and medical information related to the following:
- Appointment times
- Claims addresses
- Diagnosis codes
- FOI claims history
- Insurance plan
- Identification numbers
- Payer identification numbers
- Payment amounts
- Physician locations
The affected data varied by the patient, but could include a host of sensitive data such as Social Security numbers, dates of birth, claims addresses, insurance plan identification numbers, FOI claims histories, diagnosis codes, payer identification numbers, payment amounts, contact details, and physician locations.
The Institute is now facing a lawsuit. Morgan & Morgan filed the suit, alleging that FOI did not do enough to protect patients’ personal data and did not act fast enough when it discovered the breach.
Elite Emergency Physicians: 550,000 Patients Affected
The Indiana healthcare provider Elite Emergency Physicians experienced a data breach after it hired the third-party vendor Central Files to store and dispose of patient files. Instead of being securely disposed of, the patients’ records, including names, addresses, insurance information, and medical histories, were discovered unsecured at a dumpsite. 550,000 patients were affected by the breach.
Central files had been hired by a host of providers to destroy certain records and securely store some patient files until they were subsequently transferred to another records company, including sensitive and legally protected information.
However, reports in April warned certain providers that their documents were discovered at a dumpsite in “poor condition, showing signs of moisture damage, mold and rodent infestation, and damage from being mixed with trash and other debris.”
For Elite, the records included information of patients who visited Elkhart Emergency Physicians (ex-title of the organization) from 2002 to 2010.
There is only one conclusion we could make of it: choose associates wisely, especially those who could be dealing with sensitive data.
The biggest breaches aren’t always demonstrating the information we could extrapolate across the whole industry, though.
In the next section, we’ll explore statistics to make conclusions on patterns in data breaches.
Breaking Down the Stats around 2020 Data Breaches
The data in this section is taken from Verizon Data Breach Investigations Report 2020.
Data Breach Investigations Report usually focus more on confirmed breaches. The authors of the report admit that in Healthcare the incidents hold higher relevance than they might in any different vertical despite the data being simply “at-risk” rather than a confirmed compromise.
The pattern that tends to get lost in the shuffle is Lost and Stolen Assets: these as incidents with data being “at-risk” rather than as a confirmed compromise.
The image below shows the breakdown of the patterns for incidents in Healthcare. The Crimeware pattern includes Ransomware incidents, and as one might expect, that pattern accounts for a large portion of the incidents in this sector.
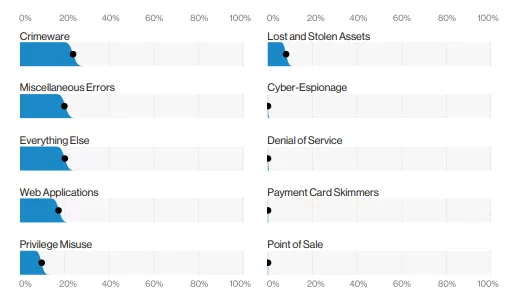
When thinking of the Healthcare vertical, one naturally thinks of Medical data. And, unsurprisingly, this is the industry in which that type of data is the most commonly breached. However, in most cases, we see quite a lot of Personal data and Credentials stolen in these attacks.
The second most common pattern for Healthcare is the Web Applications attack. As more and more organizations open patient portals and create new and innovative ways of interacting with their patients, they create additional lucrative attack surfaces.
Finally, we see a good deal of the Everything Else pattern, which is not unlike a lost and found for attacks that do not fit the criteria of any other attack pattern. It is within this pattern that the business email compromise resides.
It is typically a phishing attack with the aim of leveraging a pretext to successfully transfer money (by wire transfer, gift cards, or any other means). Although these are common attack types across the dataset, it is a good reminder to Healthcare organizations that it isn’t only patient medical data that is being targeted.
Some attacks, by their very nature, will both happen quickly and be detected quickly. A good example is a stolen laptop from the biggest case reported in 2020.
In contrast, an insider who has decided to abuse their access to copy a small amount of data each week and sell it to their buddy, who in turn utilizes it for financial fraud, may not be detected for a very long time.
The total breakdown of stats begins here. We take into account 798 total incidents with 521 confirmed data disclosures.
Most of the incidents include miscellaneous human errors: misdelivery grabbed the top spot among Error action types, while internal misuse has decreased found in web applications.
51% of data breaches happen due to external threat actors (51%), while 48% happen due to internal breaches. About 1% of all data breaches happen when threat actors have multiple sources of access to data: both external and internal.
In 77% percent of accidents, personal data is compromised, 67% of incidents include medical information stolen. In 18 percent of cases, credentials are compromised.
The authors of Verizon Research find the following ways of protection from those breaches:
- Implementing a Security Awareness and Training Program (CSC 17)
- Boundary Defense (CSC 12),
- Data Protection Protocol (CSC 13)
We’ll elaborate on it in our next publications.
Summary
The biggest data breaches do not always happen when hackers. Data could be compromised from a stolen laptop of a single employee. Following best practices in healthcare can just minimize the risk, but never avoid it entirely.
Unfortunately, breached data volumes only grow annually, and that means that there is always room for improvement in this sector of healthcare.