Almost from the very advent of distributed computing, businesses began to look closely at the opportunities provided by cloud technologies. The benefits of the cloud are well known, so it hardly makes sense to enumerate them again as cloud solutions have already proved to be profitable and convenient.
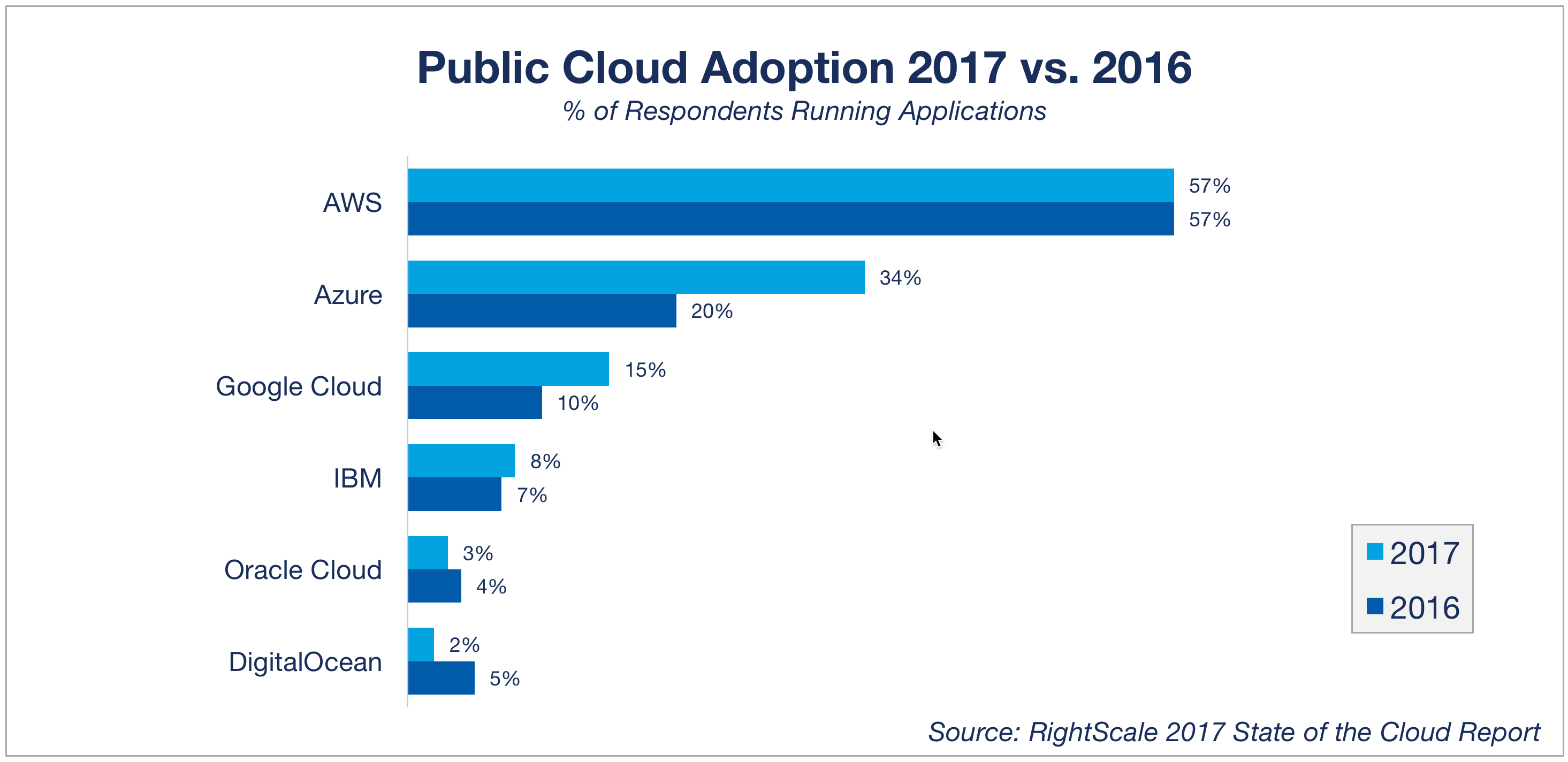
The Risks You Should Consider
However, there’s one critical point to address: companies rely on someone else’s computing resources beyond their control. This situation immediately raises questions about the availability of information. According to Frost & Sullivan, 40% of businesses across the USA claim to understand cloud computing trends but do not seem to adopt cloud services. Here’s a bunch of why’s:
- since the public service provider may experience service troubles, the access to important data may be temporarily lost or limited;
- the external provider may experience hardware or software failures that can damage information, while backup copies are not always available;
- threats to data privacy due to the lack of reliable public cloud security;
The points above give food to feed the scepticism towards public cloud solutions. CTOs often are quite critical towards the migration to distributed computing, and this way of thinking leads to the emergence of hybrid clouds which consist of private and public infrastructures. From the list of key risks mentioned above, it is difficult to single out the main one, but the most significant issue would be the problem of confidentiality. By trusting the public cloud, the organization inevitably brings its internal assets to the external environment: documents, plans, contracts, tasks, user data, etc.
Of course, it is not that easy to arrange a targeted attack on a particular enterprise because the sensitive information can be stored anywhere at the provider’s extensive and extensive data centres. However, it’s common for a potential cybercriminal to find weaknesses in the defence, and it is possible that their next intrusion attempt will affect your data. In addition, what about phishing and other attempts to impersonate a legitimate employee of the company? Therefore, when choosing a cloud solution, organizations should pay attention to the potential counterparty approaches to data security.
How to Evaluate the Reliability of the Cloud Service
If a service provider introduces a special reference section on his website to outline the security measures, it is a good sign. Especially if it’s not because of GDPR reasons, but for the sake of taking care of users who are heavily concerned about the integrity of their data.
A clear and understandable description of the protection system will allow you to evaluate the possibility of potential threats, and make sure that the developer takes his responsibilities towards the client seriously.
To solve the problem of accessibility, the cloud service must have the means to deal with troubleshooting, and be able to maintain constant uptime by reserving computing power. This is logical to expect from large IaaS vendors like Amazon or Microsoft, but as for SaaS products – you better check for this parameter, especially if providers have their own computing infrastructure or if the demand for their services is likely to exceed their existing resources.
The integrity problem is largely solved by a backup. There is no doubt that the client organization should have its own backup copies, but if the cloud provider does, well, this is a rock-solid competitive advantage. Therefore, it wouldn’t be wise for a service provider to rely on the backup copies of their clients. In case of a hardware or software failure, they have to make sure users have the possibility to work with their data at any time.
Both hardware and software should obviously procure the confidentiality of the information stored by the cloud service. To prevent an intrusion, a whole range of countermeasures is there, ranging from organisational protection of information to cryptography. The desire for a complete, comprehensive, and (ideally) echeloned protection usually shows that the service provider understands how important is to protect corporate data from an unauthorized access.
The clear policy regarding the storage of user information, coupled with the terms of its disclosure at the request of law enforcement agencies, will be a good addition as well. Besides, a cloud product should be regularly audited and have certificates confirming that the taken measures comply with industry standards and legal requirements.
Final Words
These are the basic parameters to pay attention to. However, they can say more than self-promotional service descriptions since the activity of intruders requires increased attention to security from any organization. Whatever the company does and whatever services it offers, its management should be aware of information threats and the risks of their implementation. This is especially vital for companies that base their business on working with corporate customer data as the damage from the unavailability of such information is quite serious. Therefore, it is important that every service provider treats security with increased attention. When choosing a cloud partner, you need to make sure that this particular provider is really ready to protect the information that will be entrusted to him.